Cyber criminals have started abusing legitimate Google platforms like Google Docs and Google Forms, to carry out phishing attacks that are harder to detect. They create fake or malicious sites hosted on Google’s domain to trick users into trusting phishing emails. These emails contain malicious links disguised as official Google content.
The incident
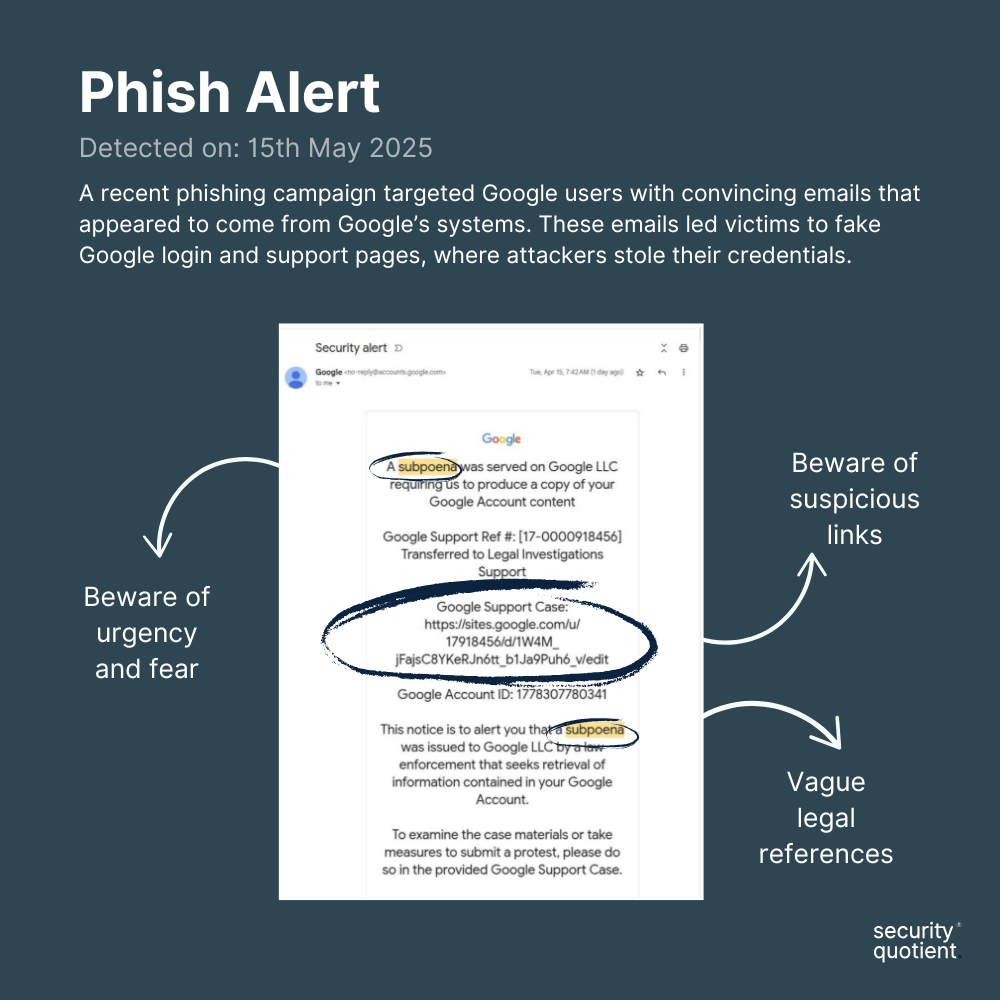
Attackers begin by creating fake websites that closely resemble Google and setting up temporary Google accounts. Using these accounts, they send official-looking emails directly from Google’s genuine email system to target users.
These emails falsely claim that law enforcement has requested access to the victim’s account data. To make the message urgent and convincing, they include fake case numbers and account details.
Because these emails are sent from Google’s own system and include its official digital signature, users find it extremely difficult to recognize them as phishing scams.
When victims click the links, they are first taken to real Google login pages, which builds trust. After signing in, they are redirected to fake support pages hosted on Google’s legitimate sites.google.com domain, where their login credentials and sensitive information are stolen.
How to spot the phishing email?
Impact of the incident
This technique highlights the growing sophistication of phishing attacks. By leveraging trusted platforms, attackers bypass many standard security filters and exploit human trust in well-known services. The attack relies on social engineering rather than exploiting software vulnerabilities, making it harder to spot and prevent.
Once attackers steal login credentials or other sensitive data, they can cause significant harm, including unauthorized access to business systems, data breaches, financial losses, and reputational damage. They can also use the stolen information to launch further phishing campaigns targeting employees, partners, or customers.
This evolving threat demonstrates that traditional defenses alone are insufficient. Organizations must focus on educating users about the risks of phishing attacks using legitimate services and improve detection strategies to identify these sophisticated attacks.
How to stay safe?
- Double-check emails that create urgency, pressure, or fear: Be especially cautious with messages claiming urgent legal requests, like law enforcement demanding your account details. Verify such emails before taking action.
- Check sender details: Confirm the sender’s email address and verify through official channels before clicking on any links.
- Verify URLs carefully: Even if a page is hosted on Google, check for any unusual requests or prompts for credentials.
- Educate employees: Continuously train staff to recognize new phishing tactics that misuse trusted platforms and emphasize cautious behavior online.
Source
Hackers Abuse Google Services to Send Malicious Law Enforcement Requests