Phishing Alert: Even Leaders are Vulnerable to Phishing Attacks
April 8th, 2025
Contributor: Aleena Jibin
Key Insight
The incident
The phishing attack began with an email that appeared to be from Mailchimp, claiming the creator’s account had been restricted due to a spam complaint. The email urged him to click a link and resolve the issue immediately without fully verifying the source. The link redirected him to a fake Mailchimp website, where he was prompted to enter his login details and a one-time passcode (OTP).
As soon as the creator entered his credentials, the attackers captured them. They had set up an automated process that quickly exported the creator’s mailing list before he could take any preventive action.
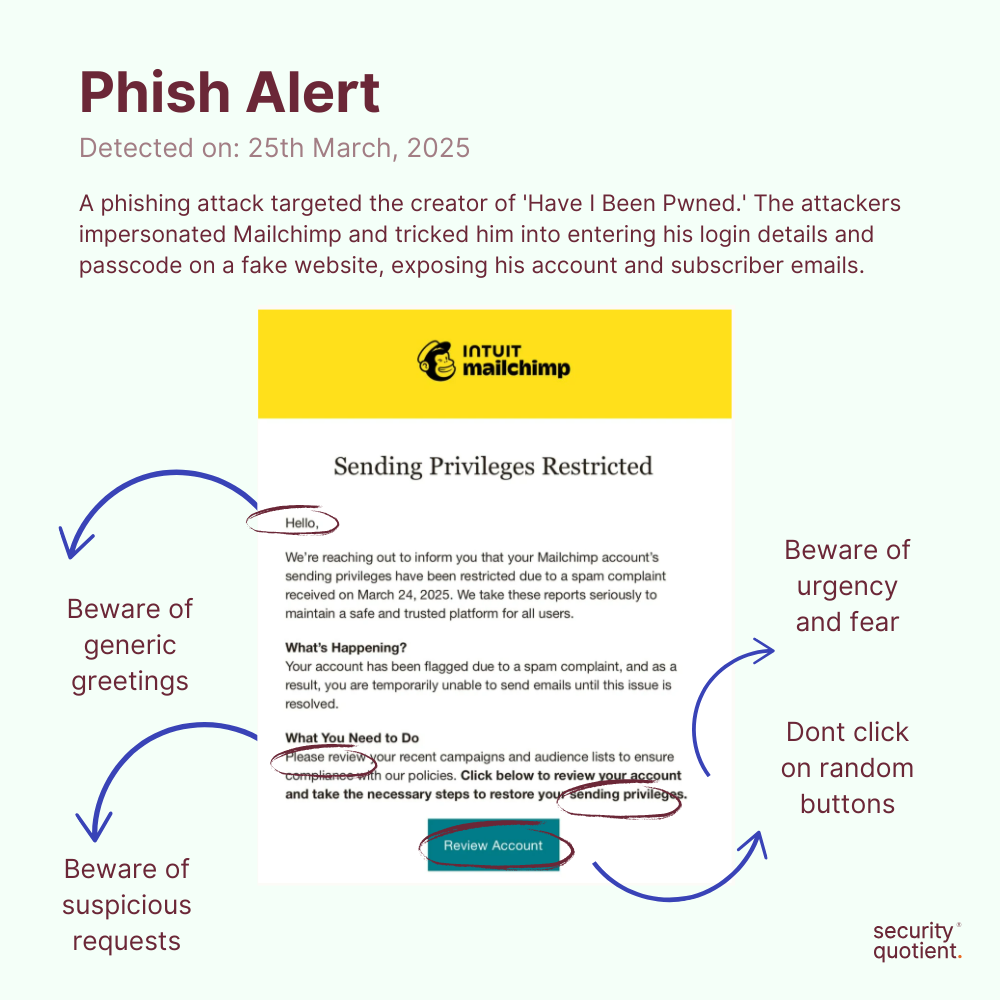
How to spot the phishing email? - Download
Impact of the incident
This attack highlights that even an expert in cyber security and phishing awareness is not immune to such tactics. The phishing scam successfully bypassed traditional security measures, relying on human error rather than technical vulnerabilities. As a result, the creator’s credentials were stolen, and 16,000 email addresses, including those of unsubscribed users, were exposed.
The incident also demonstrates how phishing methods have become more sophisticated, making them harder to detect and defend against. By exploiting user actions instead of software flaws, attackers can easily bypass security tools. The exposed email addresses, along with other personal data, could be used for further malicious activities, such as targeted phishing or identity theft.
How to stay safe?
- Stay alert to urgency and fear tactics-Phishing emails often rely on urgency and fear to trick you into acting quickly. Take a moment to carefully evaluate such messages before responding.
- Always verify the source of urgent emails-If an email seems urgent or asks for quick action, verify its authenticity by contacting the sender directly using trusted contact information before clicking any links.
- Avoid entering credentials on unfamiliar sites-Always ensure that the website’s URL is legitimate before entering sensitive information like login credentials or OTPs.
- Use stronger authentication methods-Consider using methods like passkeys or security keys, which are harder for attackers to bypass.
- Educate employees and users-Even experts can be deceived by well-crafted phishing attempts. Training staff and users on how to spot suspicious emails is essential.
Source
Even anti scammers get scammed: security expert troy hunt pwned by phishing email
