Phishing Alert: Image-Based Scams Bypassing Security Filters
February 17th, 2025
Contributor: Aleena Jibin
Key Insight
The incident
Cyber criminals are distributing phishing emails with malicious SVG files that can bypass traditional security measures. SVG files are commonly used for displaying images or graphics on websites, but they can also contain malicious code. These emails are crafted to look just like legitimate notifications you receive when someone shares a file or document with you. The message, complete with familiar branding, typically includes a link or attachment to access the shared file. It looks and feels like a typical file-sharing notification, so many people would trust it at first glance. However, if something malicious is embedded within an SVG file, it can often go undetected by traditional security tools, making it an effective method for cyber criminals to bypass defenses.
When victims open the attached SVG files, their browsers launch and automatically redirect them to phishing pages designed to steal login credentials. These phishing sites impersonate trusted platforms like Office365, Dropbox, and DocuSign, tricking users into entering usernames and passwords. In some cases, the SVG files contain embedded Base64-encoded malware that installs keyloggers, enabling attackers to monitor keystrokes and access sensitive information.
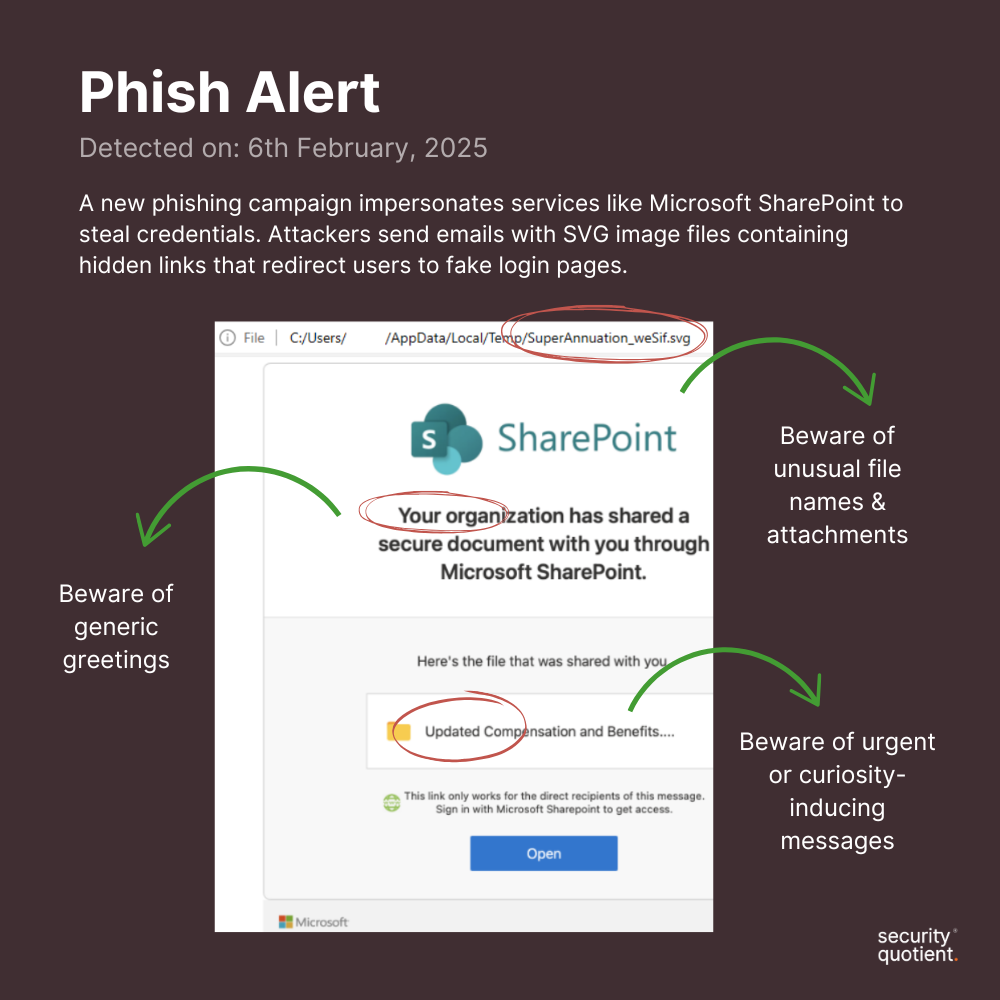
How to spot the phishing email?- Download
Impact of the incident
This campaign has significantly increased since January 2025, with thousands of phishing emails targeting businesses and individuals worldwide. Malicious actors use social engineering tactics, such as urgent subject lines like "New Voicemail" or "eSignature Required," to manipulate victims into opening these attachments. The malware delivered via these SVG files can compromise entire networks, resulting in data breaches, identity theft, and financial losses.
How to stay safe?
- Inspect attachments carefully: Avoid opening SVG files from unknown or unexpected sources.
- Check URLs before clicking: Hover over links to verify the domain. Be cautious of misspelled domains or unusual suffixes like ".ru".
- Configure SVG file handling: Set your system to open SVG files in a text editor instead of a browser.
- Report suspicious emails: Notify your IT team immediately if you receive a suspicious email. They can investigate and alert the organization to ensure everyone takes proper precautions.
Source
Weaponized SVG Files With Google Drive Links Attacking Gmail, Outlook & Dropbox Users
