How to Create a Cyber Security Change Management Plan
February 13th, 2026
Author: Indu Krishna

If you’ve landed on this post, you’re likely looking for guidance on creating a cyber security change management plan. If so, that's a great step toward strengthening your organization’s security posture. Most businesses don’t think twice before making changes to their technology.
A firewall setting gets updated to “fix an issue.”
A new antivirus gets installed because the old one expired.
These seem like everyday tasks. But in cyber security, even a tiny change can create big consequences. That’s why every business, especially SMEs, needs a Cyber Security Change Management Plan.
Think of it as a roadmap that ensures every security-related change happens safely, smoothly, and without disrupting your business. Let’s break down how to create one.
What Is a Cyber Security Change Management Plan?
It’s a simple, structured way of making sure that every change to your IT or security systems is:
- Documented (you know what’s happening)
- Reviewed (you know why it’s happening)
- Tested (you know it won’t break anything)
- Approved (you have accountability)
- Communicated (employees know what to expect)
- Monitored (you know it worked)
- Recorded (you can refer again later)
Now let’s see how to create one — step by step.
Steps to Create a Change Management Plan
1. Define the Change and Its Purpose
Start with what needs to change and why it should. Document with specificity and build the business case.
Example:
"Enable multi-factor authentication (MFA) for all employees using Microsoft Authenticator, starting with executives and IT staff. This addresses ISO 27001 audit requirement (Control A.9.4.2) for our March 2025 certification. Current gap identified in pre-audit. Non-compliance risks certification failure and potential loss of 3 key clients representing 40% of revenue."
What to Document:
- Change ID/tracking number
- Date of request
- Requestor name and department
- Urgency level (Critical/High/Medium/Low)
- Business justification (compliance, security incident, risk mitigation)
- Cost of not making the change
- Related changes or dependencies
- Timeline constraints
This gives clarity on both the action and the stakes—preventing confusion and building support for the change.
2. Identify What Will Be Affected
Every change touches something. Sometimes, it’s not immediately obvious.
List:
- Systems affected
- Users affected
- Applications affected
- Dependencies
Creating a visual diagram (when the change is complex) can help you see all interconnections, reducing surprises.
3. Assess the Risks
Risk assessment doesn’t need complex formulas. Use a simple risk matrix:
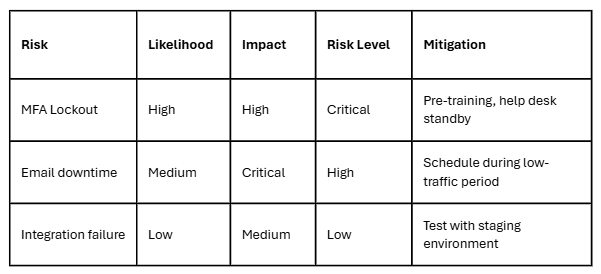
For each risk, document:
- Technical Risks: System incompatibility, data corruption etc
- Operational Risks: User productivity loss, service interruption etc
- Business Risks: Revenue impact, compliance violations etc
This helps you plan ahead instead of firefighting later.
4. Get Approval
Establish clear approval workflow, to ensure accountability. There are various ways to structure approval workflows depending on your organization's size, culture, and risk tolerance.
- Risk-Based Approval Tiers: Higher risk = higher-level approval
- Peer Review Model: Changes approved by IT team members
- Change Advisory Board (CAB): Weekly meetings to review changes
- Agile Approach: Daily stand-ups where changes are discussed and approved informally
5. Prepare a Rollout Plan
A solid rollout plan answers the following:
- Who will perform the change
- When it will happen
- Estimated downtime
- Step-by-step instructions
- A fallback / rollback plan
A well-documented rollout plan minimizes risk and ensures everything runs smoothly.
6. Test Before Rolling Out
Testing helps you catch errors early. A small test saves hours of disruption.
Example: Test MFA for 3–5 users, not the whole company
Testing Checklist Example (MFA Implementation):
- Can users enrol successfully?
- Do all authentication methods work (app, SMS, hardware token)?
- Can users access all required applications after enabling MFA?
- Is help desk trained to support MFA issues?
- Are backup codes being generated and stored securely?
Document Test Results:
- What worked perfectly
- What needed adjustment
- What failed completely
- Unexpected issues discovered
- User feedback summary
7. Implement the Change Carefully
Apply the change according to your plan. Preferably during low-traffic hours, weekends, or off-peak shifts. Document everything you do during the implementation.
8. Verify the Change Worked
Check:
- Are systems running normally?
- Are employees able to work?
- Are there any errors?
- Are logs clean?
For significant changes, monitor the systems for 24–48 hours.
9. Communicate With Everyone Affected
Communication prevents panic. Example message:
“Tonight from 6 PM to 7 PM, we will enable MFA on employee accounts. You may need 5 minutes tomorrow to set it up. Please install the Microsoft Authenticator app in advance.”
Clear communication = fewer complaints + smoother adoption.
10. Document Everything
Even simple changes should be documented. This helps if something goes wrong later, if you need to make a similar change in the future, or during audits.
A simple log is enough:
- What changed
- Who approved
- Who implemented
- What issues occurred
- How it was fixed
Why Do You Need a Change Management Plan?
Imagine this situation. An employee from your IT department updates the email security filter to block more spam. Good idea, right? Except the next morning:
- Employees cannot access important vendor emails
- OTP messages for banking are blocked
- HR onboarding mails sit in quarantine
- Clients complain their emails are bouncing
- Your team loses half a day trying to figure out what broke
The change wasn’t wrong. The process was.
The update to the email security filter was a valid action to reduce spam. However, the lack of planning, testing, and communication turned a simple change into a disruption.
A well-planned change management strategy prevents these headaches by ensuring changes improve security without harming productivity.
A Simple Change Management Template
Here’s a beginner-friendly template to get you started:
Change_Management_Template.docxMake Security Changes Safely
A cyber security change management plan isn’t about making things complicated — it’s about making changes safely. In today’s fast-evolving cyber world, a structured approach ensures you strengthen your security without introducing new risks.
