Featured as an emerging Company to Action in The Frost Radar – 2020 and 2022.
Our Solutions
Address the human factor in cyber security through our Assess, Train and Analyze model.
Assess
Identify Risky Cyber Behavior
Blind Spot Assessments
Assess employee cyber security awareness and competencies before onboarding or allocating the workforce to projects with critical cyber security requirements.
Culture Surveys
Assess and understand the prevailing attitudes, sentiments, and awareness related to cyber security within your organization across various job roles.
Mock Phishing Assessment
Test employee vigilance to counter phishing attempts through simulated or gamified assessments and fortify your defenses against evolving phishing threats.
Train
Build Positive Cyber Security Behavior
Gamified Courses
Enhance your team with Gamified E-Learning Courses. Encourage positive cyber security behavior through the reward-penalty model, rewarding the correct choices and penalizing mistakes.
Security Awareness Nuggets
Provide ongoing, bite-sized lessons to boost security consciousness and keep your employees vigilant amidst the constantly changing cyber threat landscape.
Analyze
Evaluate And Improve Behavior
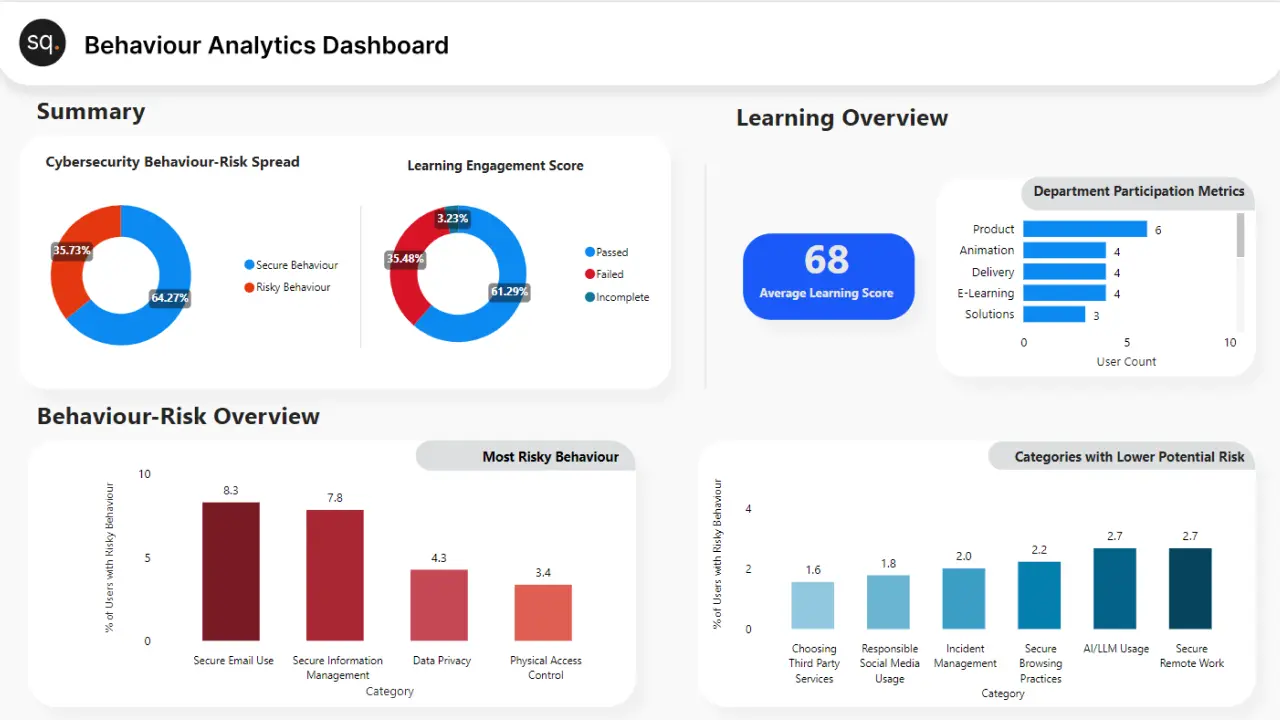
Cyber Behavior Data Analytics
Interpret data from cyber security Behaviour Assessments, Culture Surveys, Phishing Assessments, and Gamified Courses. Review and understand the prevailing attitudes, sentiments, awareness levels, and behavioral trends, employing these findings for the continuous improvement of the cyber security awareness program.
Unique features that meet your specific needs
Tailor-made plans
Secure a plan customized to your budget, free of long-term lock-ins and lifetime licensing of content, all within our personalised service offerings.
Customized Content
Tailor the training material to match your company’s brand, security protocols, data classification guidelines, incident reporting methods and more.
Multilingual translation
Ensure that cyber security training is available to all employees by providing authentic translations in multiple languages, each done by native speakers.
Private learning platform
Acquire a secure learning environment that prioritizes sensitive user data protection with dedicated databases in your chosen AWS or Azure region.
Latest Courses and Assessments
Explore the newest offerings from our cyber security researchers, learning, and data science team.
Information Security and Indonesia Personal Data Protection Law
Elevate awareness for safeguarding personal data in accordance with Indonesia PDPL.
Cyber Security for Business Leaders
Build strong cyber security leadership skills using a case-study-driven course.
Data Protection and Privacy
Drive employee awareness to protect customers’ and employees’ personal data.
Create your plan
within your budget
Flexible Pricing
Unlike rigid pre-set SaaS packages, enjoy the freedom to customize your annual cyber security program according to your specific requirements and pay only for essential solutions.
Get Pricing

About Security Quotient
Protecting organizations from cybercrime by enhancing human cyber attack resilience through cyber security awareness, behavior, and culture management solutions.
2005
Incorporated
25
Client Countries
ISO 27001
Certified
27
Languages
Check our latest resources
Explore our knowledge base that brings together content highlighting the latest tools, exploits, technologies, and insights in the cyber security industry.

Creating a GDPR-aligned Cyber Security Awareness Training Program
Role of Behavior Indicator Map in Cyber Security Data Analytics

Building Human Cyber Resilience using Security Awareness Training Programs
Frequently Asked Questions
General
Absolutely. We customize the training courses and content to align with your organization’s security policies, compliance targets, data privacy laws, and brand tone. This ensures higher employee engagement and effectiveness.
Our service includes a variety of engaging Gamified Courses, Culture Surveys, Behaviour Assessments, Security Awareness Nuggets, and Anti-Phishing Training. These are hosted on a dedicated, secure learning platform and are designed to cater to diverse learning preferences.
Yes, we provide a Dedicated Client Manager and a responsive Support Desk to assist with course launch, reminders, troubleshooting, and any other support needed to achieve your cyber security training goals.
Yes, we provide a complimentary 30-minute free consultation service to help you explore and understand the offerings of our Cyber Security Awareness Training services.